On September 8, 2025, The U.S. Treasury Department announced sanctions against nine Myanmar entities and ten Cambodian entities for forcing human trafficking victims to participate in cryptocurrency investment scams.
"Southeast Asia's cyber scam industry not only threatens the well-being and financial security of Americans, but also subjects thousands of people to modern slavery," John K. Hurley, Under Secretary of the Treasury for Terrorism and Financial Intelligence, said in the statement.
The anonymity and cross-border nature of cryptocurrencies have increasingly become fertile ground for transnational financial crime. The U.S. Department of Justice (DOJ) has recently disclosed two major international money-laundering cases involving virtual assets, with combined proceeds exceeding 💲10 million. These prosecutions expose industrialized criminal operations and reveal compliance gaps at some financial institutions and exchanges.
As a Web3 security firm, BlockSec used MetaSleuth (metasleuth.io) to perform tracing analysis and draw industry lessons from these cases.
Case 1 — $73M Laundered Through Shell Companies
In May 2024, a federal grand jury indictment in the Central District of California charged Daren Li, 41, and Yicheng Zhang, 38, with conspiracy to commit money laundering and six substantive counts of international money laundering.
According to the indictment, Li, Zhang, and co-conspirators ran an international syndicate that laundered proceeds from cryptocurrency investment scams—commonly known as “pig butchering.” Victims were induced to transfer millions into U.S. bank accounts opened in the names of dozens of shell companies created to facilitate laundering.
More than $73 million of fraud proceeds were moved through U.S. financial institutions to accounts at Deltec Bank in the Bahamas, converted to Tether (USDT), and transferred to virtual asset wallets. A cryptocurrency wallet tied to the scheme received more than $341 million in virtual assets.
If convicted, Li and Zhang face a maximum penalty of 20 years’ imprisonment on each count. 👉 DOJ press release: https://www.justice.gov/usao-cdca/pr/two-foreign-nationals-arrested-laundering-least-73-million-through-shell-companies?utm_source=chatgpt.com
An indictment is merely an allegation. All defendants are presumed innocent until proven guilty beyond a reasonable doubt in a court of law.
Case 2 — $36.9M Scam; 51-Month Sentence
In September 2025, Shengsheng He, 39, of La Puente, California, was sentenced to 51 months in federal prison and ordered to pay $26,867,242.44 in restitution for his role in an international digital-asset investment scam conspiracy operated from scam centers in Cambodia.
He had pled guilty in April to conspiracy to operate an unlicensed money-transmitting business.
Court filings describe a familiar pattern: co-conspirators overseas contacted U.S. victims via unsolicited social media interactions, phone calls, text messages, and online dating services, lured them with promises of high returns on digital-asset investments, and induced victims to transfer funds that were in fact stolen. More than $36.9 million in victim funds were routed through U.S. shell companies into a single Deltec Bank account in the Bahamas, opened in the name of Axis Digital Limited (a company co-owned by He). Those funds were converted into USDT and sent to wallets controlled by Cambodian scam operators. From there, funds flowed to scam centers in Sihanoukville and other locations.
To date, eight co-conspirators have pleaded guilty, including Daren Li and Lu Zhang, who each admitted to conspiracy to commit money laundering in 2024. Axis Digital co-founder Jose Somarriba and director Jingliang Su also pleaded guilty to conspiracy to operate an unlicensed money-transmitting business. 👉 DOJ press release: https://www.justice.gov/opa/pr/california-man-sentenced-role-global-digital-asset-investment-scam-conspiracy-resulting?utm_source=chatgpt.com
Deltec Bank as a Recurring Laundering Hub
A striking commonality is the repeated use of Deltec Bank in the Bahamas as a fiat-to-crypto conduit:
-
In the Li/Zhang matter, funds moved from U.S. shell companies into Deltec accounts, were converted to USDT and routed to crypto wallets tied to the scheme.
-
In the He matter, $36.9M in victim funds were concentrated into a single Deltec account (Axis Digital Limited), converted to USDT, and then transferred to Cambodian scam wallets.
Deltec, as a regulated offshore bank, was expected to implement robust AML measures. Instead, these cases illustrate how compliance lapses at some offshore institutions can create critical vulnerabilities that criminal networks exploit to convert illicit fiat proceeds into virtual assets.
What U.S. Enforcement Actions Reveal
These prosecutions and the Treasury’s sanctions illustrate a multi-faceted U.S. response:
-
Top-level commitment. Senior officials including Attorney General Martin Estrada and Deputy Attorney General Lisa Monaco publicly condemned pig-butchering scams and signaled sustained enforcement priorities.
-
Multi-agency coordination. Investigations involved the U.S. Secret Service’s Global Investigative Operations Center, the Homeland Security Investigations’ El Camino Real Financial Crimes Task Force, Customs and Border Protection’s National Targeting Center, the U.S. Department of State’s Diplomatic Security Service, the Dominican Republic National Drug Directorate Sensitive Investigative Unit, U.S. Marshals Service, Drug Enforcement Administration (DEA), and the Justice Department’s Office of International Affairs, demonstrating the cross-border, multi-agency collaboration necessary to combat transnational crypto crimes.
-
Specialized enforcement. Prosecution was led by Assistant U.S. Attorneys Maxwell Coll and Alexander Gorin of the Asset Forfeiture and Recovery Section, Nisha Chandran of the Cyber and Intellectual Property Crimes Section, and Trial Attorney Stefanie Schwartz from the National Cryptocurrency Enforcement Team (NCET) within the Criminal Division’s Computer Crime and Intellectual Property Section (CCIPS). The NCET focuses on investigating and prosecuting the illicit use of digital assets, particularly within cryptocurrency exchanges, mixing services, and infrastructure providers. Since 2020, CCIPS has secured convictions of over 180 cybercriminals and obtained court orders for the return of over $350 million in victim funds.
BlockSec MetaSleuth Findings
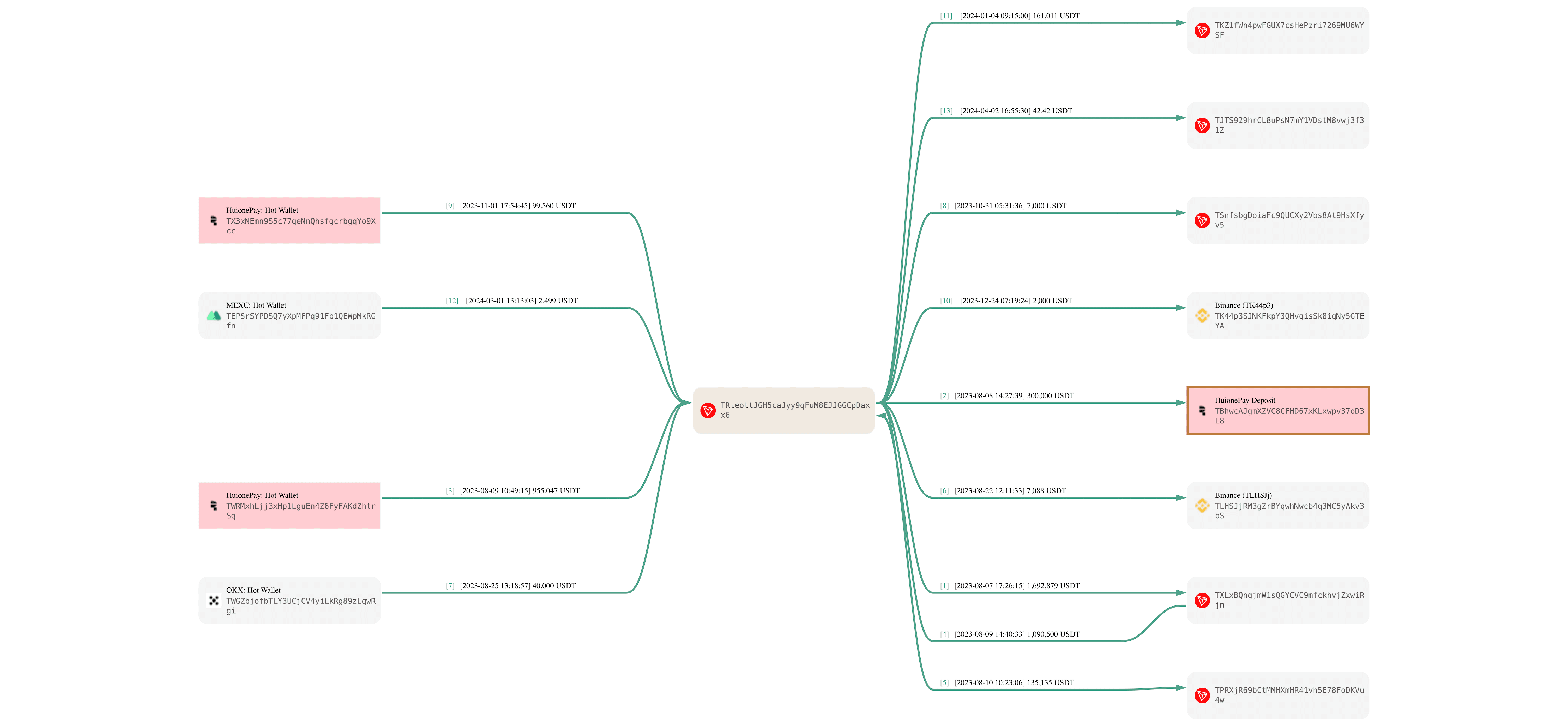
DOJ filings referenced a suspicious address labeled in public filings. Using our proprietary intelligence and AI-driven fuzzy matching, BlockSec identified the address TRteottJGH5caJyy9qFuM8EJJGGCpDaxx6 and conducted an in-depth on-chain analysis:
-
Scale: Over 10,000 transfers involving more than 700 counterparties, with aggregate inflows/outflows exceeding $300 million.
-
Patterns: Average inbound transfers of roughly $30,000 (indicative of retail victim payments) versus average outbound transfers of approximately {{text}}30,000 (evidence of consolidation by laundering networks).
- Counterparty links: Material value transfers to and from major exchanges such as Kraken, Binance, FTX, and transactions involving underground payment services like Huione Pay. Some high-value transfers were only one hop from mainstream exchanges yet were not detected promptly—highlighting delays and gaps in current intelligence updating and monitoring.
These observations underscore a frequent problem: by the time many compliance systems raise alerts, illicit funds have already moved through complex layering steps, diminishing the chance of effective intervention.
Visualize the TRteo address fund flows ⬇️
Industry Recommendations: Technology, Compliance, and Awareness
These cases exemplify the industrial scale and cross-border reach of contemporary crypto fraud. To mitigate such risks, stakeholders should adopt a three-pronged strategy:
- Enterprises:
Strengthen real-time AML/CFT capabilities and chain forensic skills. Platforms should integrate automated screening (e.g., Phalcon Compliance) at onboarding and transaction points and use deep forensic tools (e.g., MetaSleuth) for incident response and tracing—creating a closed loop of real-time detection + deep tracing.
- Investors:
Beware unsolicited offers promising guaranteed high returns. Preserve transaction hashes and communications, and report fraud promptly to local law enforcement to aid tracing and restitution.
- Regulators:
Expand cross-border cooperation and embrace RegTech: shared illicit address lists, real-time monitoring, and joint investigative frameworks are critical to curbing global crypto abuse.
Conclusion
Cryptocurrency is a neutral technology; when weaponized for fraud and money laundering it not only harms victims but also undermines trust in the broader ecosystem. BlockSec believes that only a combination of technical tracing, robust compliance, and public awareness can restore safety and trust in Web3.




